The U.S. Department of Health and Human Services has noted a rise in health care cyber-attacks. Additionally, NIST has new guidance to help organizations comply with the HIPAA Security Rule. Special Publication adds Endpoint Detection and Response (EDR) as an additional safeguard to consider. It can mitigate against ransomware and other advanced threats that are overwhelming the security and IT staff across the healthcare industry. But technology alone isn’t going to solve this problem. MDR is Managed Detection and Response, a service that incorporates EDR technology, and the expertise has the potential to change the outcomes across healthcare organizations.
Compared to other industries, healthcare has the most diverse use of IT, digital innovators, and the most diverse organizations, from small practices to integrated care networks, contributing to this problem. There are plenty of options as the market is growing and evolving but finding the right fit for each organization takes time. MDR is not the same across every provider, and it makes sense to understand the origins and evolution since there is really not a one size fits all.
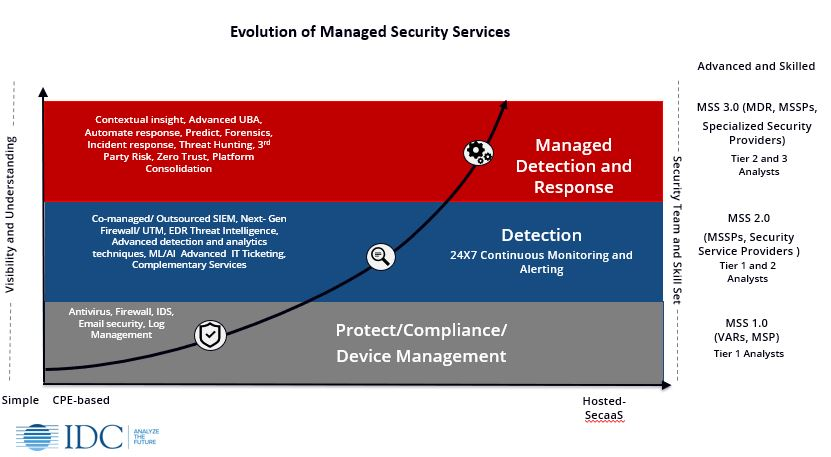
From IDC, the evolution of Managed Security Services ranges from device management to the more advanced and skilled managed detection and response.
Some top-tier MSSPs (Managed Security Service Providers) would have you believe that their value is in being able to manage your new [insert cool technology product name here], or existing security stack, in your environment on your behalf. The clients get the most value from their past investments and the ability to now re-deploy staff onto other projects. This works for large enterprises or healthcare organizations that have invested in technology but need assistance in extending their security operations.
Across the industry and organizations, human capital is constrained and could be better utilized by focusing on higher-order business and other initiatives. Security expertise and threat-hunting analysts are in premium demand. The various models and growth in the MSSP industry are being fueled by the ability to serve organizations of all sizes, helping them to achieve better security outcomes.
Moving a client from a basic security framework, an MSSP can immediately advance the company’s protection and detection capabilities to those of a much larger organization. Considering the several types and models for MSSPs, companies should aim for those who do more than just take on basic security. Those that have architected for the highest tier from the IDC chart can give advantages to smaller companies that did not or could not invest in security technology in the past. Providing managed detection and response from all angles of security operations increases the visibility into malicious behavior and threat-hunting details needed to act quickly. Ideally, an MSSP should be able to provide service across the following assets:
Endpoints: The largest attack surface comes from end-user laptops and workstations, especially with the shift to remote work.
Servers: The most critical systems in your organization.
Network: The point that gives the widest access to your company’s resources.
Specialized security providers have proliferated around each of these pillars, along with providers of log management with threat detection. Some vendors of these solutions have created MSSP units to provide the management, maintenance, and response to events and incidents on behalf of their customers. However, because they are focused only on one area or leveraging point solutions, they cannot move quickly to provide broader security and threat detection coverage through a comprehensive end-to-end security solution.
Everyone can agree that focusing on detection and response is critical to act and mitigate before any damage is done quickly. Here is a simple breakdown of what this requires – without getting into technology acronyms.
- Especially in healthcare, 24×7 active security operations coverage is needed to ensure systems stay available and protected.
- Proactive threat hunting vs. responding to security alerts
- Extended access across the spectrum of security data vs. looking at only specific security events
You may recognize this as Extended Managed Detection and Response (XDR), or you may not. Some believe that XDR refers to a platform that facilitates these services provided by a single security solution vendor. Others believe this is an evolutionary step that XDR can fulfill, but the promise of Security Incident and Event Management (SIEM) solutions fell short. This can be a vendor delivering a platform that integrates the extended security events into view for threat hunting activities. And, of course, there are several other assumptions about what XDR represents. I am pointing this out as many service providers focus on providing XDR, and there is no clear and common definition in the market these days. It is not the silver bullet to solve all security problems.
Healthcare organizations must assess and address how best to counter the growing threats and attacks when they are also struggling with:
- Building out and staffing security operations 24/7/365
- Hiring and retaining experienced security analysts
- Security spending keeps growing, but security incidents have not decreased
- Even with an MSSP, there are too many alerts, but few answers
- Not having visibility into what my provider is doing and interpreting the level of risk of an incident
To help healthcare organizations, we are growing our Clearwater family by acquiring TECH LOCK Inc., a provider specializing in managed security and integrated compliance. Together we are expanding the services we can provide to healthcare organizations, including MDR, with extended security signals to bring cost-effectively and significantly improved security outcomes to our clients.
We have put together a guide with 5 Tips on How to Evaluate an MSSP. It gives details on what to expect and what to ask if you are looking to explore an MSSP/MDR option.



