IRM|405(d) HICP™
Demonstrate your organization’s use of recognized security practices, like 405(d) HICP.

We Can Help
You’ve worked hard to establish recognized security practices of 405(d) HICP. Still, for an OCR investigation, you must also demonstrate that these healthcare cybersecurity practices have been in place for at least 12 months.
IRM|405(d) HICP helps you assess and show your implementation of Recognized Security Practices defined in the 405(d) Health Industry Cyber Security Practices (HICP) Guide by identifying program and process gaps and informing remediation planning.
Run an assessment against the 10 best practices relative to your organization’s size.
Realize the benefits outlined in 405(d) HICP, one of two recognized security practices under Public Law 116-321, an amendment to the HITECH ACT.
IRM|405(d) HICP displays findings in a dynamic dashboard. All assessment documentation is available in a central, secure location and can be used to prepare for an audit or investigation.
By law, the Department of Health and Human Services (HHS) must consider these recognized security practices when making specific determinations in conjunction with an audit or investigation and for other purposes.
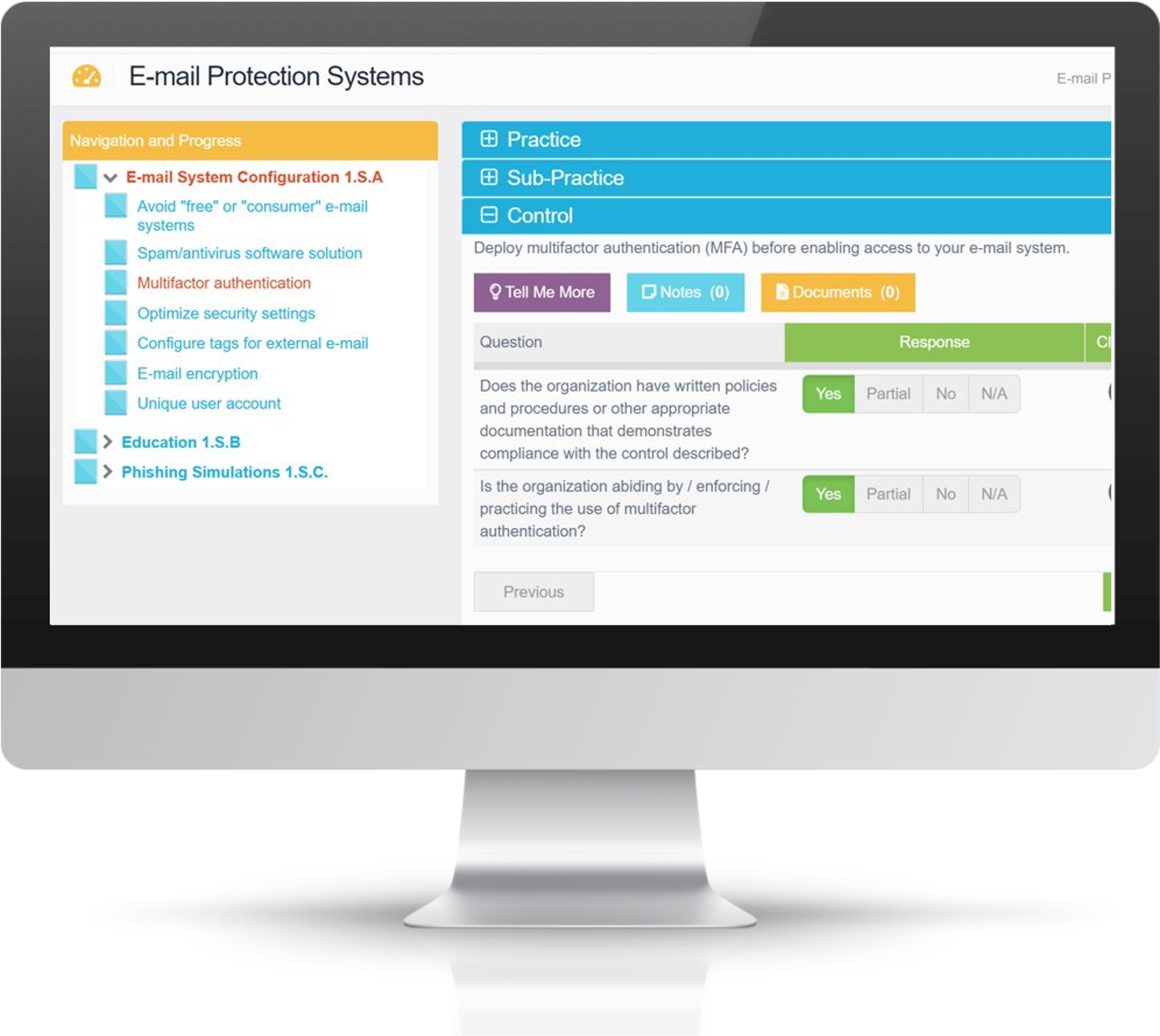
Assessment Wizard
Walks the assessor through the process in an easy-to-use interface
Relative Assessments
For small, medium, or large health organizations, as categorized by the HICP Guide
Dynamic Updates to Your Executive Dashboard
Consolidated Findings/Gaps
Easily managed and tracked through remediation steps
Documentation Storage & Prep
Stored in a central, secure location
See the Clearwater Difference
405(d) HICP Assessment
Our 405(d) HICP assessment includes an evaluation and documentation of how your organization is following the sub-practices of all ten cybersecurity practices as relevant for your organization’s size: small, medium or large.
Connect
With Us
