From new applications that help manage patient care delivery to a growing number of innovative technologies now integrated into healthcare, it can be challenging for security and compliance teams to get their arms around new and emerging threats.
On top of that, there are known exploits, necessary patching, system and software updates, and misconfiguration issues they must tackle continuously.
Even with dedicated teams and reliable threat intelligence, teams often struggle with prioritizing what needs attention first, leaving some vulnerabilities unidentified and unaddressed.
The vulnerabilities hiding in plain sight can be the easiest ones to overlook.
Operational resilience often relies upon being able to answer these questions:
- Which threats exist that are unique to our organization?
- What is their potential impact on important services?
- What can we do to minimize their impact?
Vulnerabilities Hiding in Plain Sight
The vulnerabilities in plain sight across your attack surface can often have potentially grave financial impacts. A cyberattack can cause damage ranging from downtime and loss of services to potential regulatory, legal, and civil fines, on top of all the costs associated with response and recovery.
When unchecked, vulnerabilities can ultimately have long-lasting negative impacts on operations.
And there are many-the Cybersecurity Infrastructure & Security Agency (CISA) is tracking more than 870 known vulnerability exploits.
How might some of these exploits affect your healthcare organization? Here are a few examples:
- Data breach and loss
- Extortion
- Destruction
- Mortality and patient safety
- Business impacts
- Reputational damage
Threat Actors: Who Are They and What Do They Want?
Threat actors are known to target healthcare; the industry ranks above energy and utilities and aerospace and defense in number of cyberattacks.
Why is healthcare in attackers’ crosshairs?
Primarily, it’s because their attacks have been successful-and they’re often lucrative. And unfortunately, if you look at the growing number of attempted and successful breaches over the past 18-24 months, it may give the impression that this is an issue healthcare is not taking seriously enough.
What’s happening?
While threat actors come in various forms with various motivations, we are seeing significant impact from state-sponsored advanced persistent threats (APT) and other financially motivated cybercriminal groups.
These threat actors run their operations as enterprises using various tools and tricks, for example, exploiting web applications, which is a leading attack vector for healthcare.
Web applications play a big role in delivering information service business functions, and a result, they are also among cyberattackers’ favorite means for stealing credentials. Attackers look for vulnerabilities that enable them to steal credentials and then move across your network and connected devices, taking advantage of non-remediated vulnerabilities.
Some of the top malware families are designed specifically to steal credentials through web services, and more than 70% of hacking actions have been on web applications.
According to Verizon’s 2022 Data Breach Investigations Report, there were 849 incidents involving web application attacks in healthcare, with 571 confirmed to have had data disclosures in 2021. These attacks can impact the confidentiality, integrity, and availability of healthcare systems, data, and more.
These threat actors often hide in plain sight, and their attack methods commonly look like this:
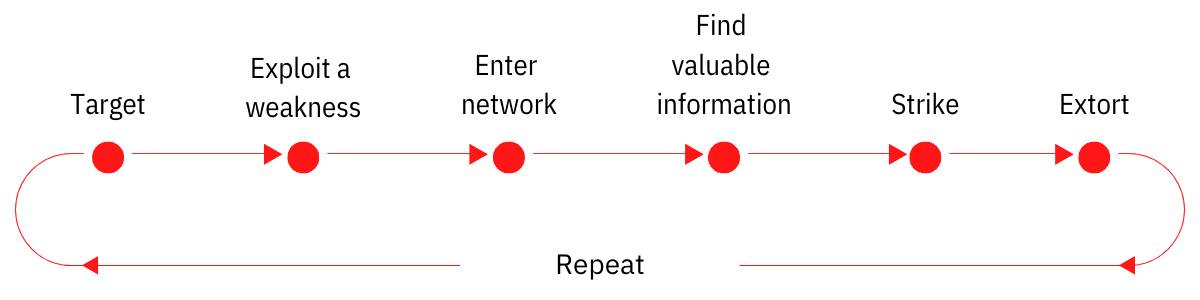
The Greatest Threats in Your Attack Surface
Regarding credential theft, it’s important that every person in your organization understands that they are part of your attack surface and at risk of being targeted.
It doesn’t matter what role someone plays within your organization; they should be aware of your organizational risks and how these threats can impact their jobs and the organization. And they need to be well-trained and educated on basic cyber hygiene and compliance best practices.
This is more challenging today with remote workforces as remote teams introduce a range of new security risks. It’s not uncommon to encounter instances where employees struggle to keep work and personal identities and access separate; with the interconnectivity of devices and networks, risks grow exponentially.
These vulnerabilities extend beyond your employees.
Looking at the expanding attack surface and what’s often targeted successfully, more focus is needed within the supply chain, all the way down the vendor list. It’s no longer enough to know what your first-tier vendors are doing in terms of security and compliance. Due diligence is necessary for every vendor that can access your sensitive and protected data.
When seeking out often overlooked vulnerabilities within the supply chain, it’s important to first identify:
- Who accesses our data?
- How do they use it?
- What are they doing to keep it safe?
Trusting the wrong partner can have long-lasting consequences. Ask yourself:
- How confident are you in knowing who has access to what?
- Do you know how a vendor breach could impact your organization?
- Do you know what to do if an attacker compromises a vendor?
How to Address Cyber Threats Hiding in Plain Sight
So, with a better understanding of some security risks that often hide in plain sight, what steps can you take to address these cyber risks?
Here are a few recommendations:
Identify, track and manage all assets.
Remember, you cannot protect what you don’t know about. As healthcare organizations become increasingly interconnected, it’s important to maintain visibility into your assets.
You should also implement a robust vulnerability management program. Seek out vulnerabilities for all your assets and remediate or mitigate those risks as quickly as possible to ensure threat actors cannot take advantage of them.
This isn’t a one-time process. To reduce cyber risk, you must continually assess and address risks.
Train and educate every single employee.
People are a key attack vector. Generally, that’s whom attackers target first and often how they get in. Because of that, you cannot train and educate your people enough.
But beyond that, you must also implement and validate appropriate security controls. If you haven’t already, start with multi-factor identification and privileged access management.
Attackers can’t hide in your network if you have the right controls and have implemented best monitoring practices.
These are small steps you can take to minimize a breach’s impact on your organization. Not only do these steps improve your risk posture, but they can also help with cyber insurance premiums.
Understand how your supply chain impacts your business processes.
Regarding your supply chain, consider conducting a vendor risk analysis to determine where risk exists within your supply chain and the potential impact on your organization. Leverage a lifecycle management approach so you always have insight into threats along your supply chain, no matter how much it expands or how often it changes.
The Takeaway
As the healthcare threat landscape expands and becomes increasingly complex, it will continue to challenge security teams as they work to seek out and address risks across your evolving attack surface. However, several key steps, like conducting OCR-Quality® Risk Analysis and implementing continuous risk management processes, can help you more effectively identify known and unknown vulnerabilities so you can build confidence that you’re doing everything you can to secure and protect your healthcare systems and data.
Not sure where to start? We can help.
No one knows healthcare cybersecurity like Clearwater. Our deep bench of cybersecurity experts can help you uncover hidden vulnerabilities and develop the right strategies to address them. Whether you need help in the short term or a partner to help you manage cyber risk and compliance on an ongoing basis, we can tailor a solution to meet your unique business needs. Learn more.



