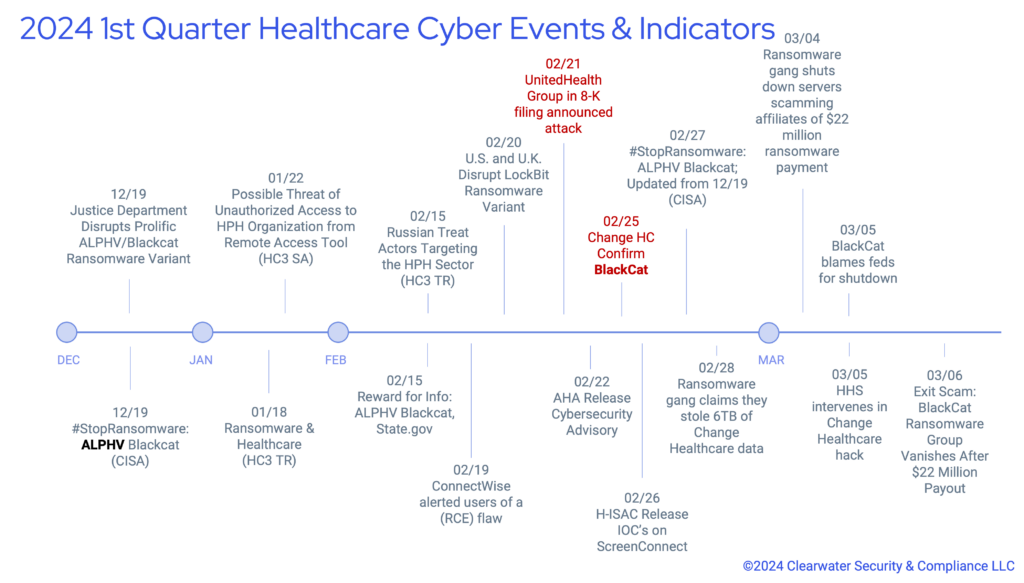
More than a month after a ransomware attack targeted Change Healthcare and its connected partners, the healthcare industry is still grappling with recovery from what some analysts are calling the “biggest ever” cyberattack on the U.S. healthcare system.
Who is Change Healthcare?
Change Healthcare is a health-related technology company that provides various services for healthcare organizations, ranging from payments and claims management to patient engagement. The technology connects providers, payers, and patients and provides data analytics and other services to improve patient/provider engagements across healthcare.
According to TechTarget, the company is one of the largest healthcare information exchange platforms in the nation, handling 15 billion claims each year at about $1.5 trillion.
What Happened?
The Change Healthcare ransomware attack has left many providers unable to process payments, impacted provider workflows, limited patient access, and, in some cases, prevented pharmacies from processing prescriptions.
On Feb. 21, UnitedHealth Group (UHG), which owns Change Healthcare and its Optum business platform, announced Change’s systems were breached and responded by disconnecting Change systems.
The ransomware group BlackCat, or ALPHV, appears behind the Change Healthcare breach. BlackCat has previously been linked to two other ransomware as a service (RaaS) groups, DarkSide and BlackMatter. DarkSide was behind the Colonial Pipeline attack.
What We Know
Many attack details remain unclear, such as whether any patient’s health information (PHI) is affected. Still, UHG has indicated it is working with law enforcement and security experts like Mandiant and Palo Alto Networks. They are in the process of restoring functionality and conducting forensic analysis on the attack itself. The company estimates a payment platform will be ready for connections on March 15, with testing and re-establishing connectivity to a claims network and software targeted for March 18. Electronic prescribing services and the Change Healthcare Pharmacy Network appeared to be back online as of March 8.
UHC’s website indicates that, at this time, there appears to be no evidence of lateral attack movement outside the Change Healthcare environment though on dark web forums, BlackCat affiliates who claim to have carried out the attack dispute this.
Some reports indicate that Change Healthcare may have made a $22 million ransomware payment to BlackCat for an encryption key and to prevent the potential release of terabytes of data. After payment, BlackCat appears to have shut down its servers, pulling off an exit scam and attempting to sell the malware’s source code for $5 million.
Industry Response
Following the attack, many leading industry governance and regulatory agencies released bulletins and reports to help healthcare organizations respond and prevent additional impact.
Health-ISAC issued a bulletin aligning the attack with exploitation of ConnectWise ScreenConnect vulnerabilities CVE-2024-1708 and CVE-2024-1709. On Feb. 19, ConnectWise announced a remote code execution (RCE) flaw that threat actors could leverage to bypass authentication in ScreenConnect servers. It advised users to patch to avoid potential RCE compromise immediately. BlackCat claims they didn’t exploit the ScreenConnect vulnerability to gain initial access in the same dark web discussion board where they insist their attack is not in fact limited to Change Healthcare.
The American Hospital Association (AHA) has also released cybersecurity advisories about the attack’s indicators of compromise (IoCs), urged users to disconnect from Change Healthcare and Optum, and to:
- Test the security, redundancy, and resiliency of networks and data backups
- Patch all high criticality, known, and exploited vulnerabilities, especially those that are internet-facing
- Review and test cyber incident response plans
- Review business and clinical continuity downtime procedures
- Consider designating clinical downtime coaches and safety officers
- Increase threat hunting and monitoring tools and techniques
The Cybersecurity and Infrastructure Security Agency (CISA) issued its
#StopRansomware: ALPHV Blackcat cybersecurity advisory on Feb. 27 encouraging organizations to:
- Routinely take inventory of assets and data to identify authorized and unauthorized devices and software
- Prioritize remediation of known exploited vulnerabilities
- Enable and enforce multifactor authentication with strong passwords
- Close unused ports and remove applications not deemed necessary for day-to-day operations
What Does This Mean for You?
To know and understand your risk, you have to know your adversary. The AHA cites the FBI indicating that by late 2023, ALPHV Blackcat affiliates had compromised more than 1,000 entities and received more than $300 million of its demanding $500 million in ransom payments.
That’s why it’s essential to take note of industry-issued cybersecurity advisories, such as those about indicators of compromise. This will help you better understand the actual threat and build effective response and action plans.
To understand a threat assessment and the characteristics of a threat actor, you have to look at their capabilities and intent:
- Are they targeting you?
- What’s the relevance?
- What’s the likelihood of that attack?
Lingering Threats
Just because BlackCat appears to have taken its servers down doesn’t mean there’s nothing left to worry about. There is still a viable threat. These types of threat actors often pop up again and frequently use similar kinds of IoCs.
Blackcat, for example, is known to use social engineering like emails, phone calls, and texting to try to gain initial access—it’s a sophisticated attack method and still the most common attack strategy among cyber criminals. Once they get an initial foothold, they use various techniques to bypass protections, such as multi-factor authentication (MFA), to access credential troves.
Once an attack is successful, other threat actors are often eager to do the same and will try to take advantage of similar IoCs for additional attacks elsewhere. Healthcare organizations should be aware of potential scams that may take advantage of the Change Healthcare incident, especially in terms of social engineering and phishing campaigns to attempt to steal credentials and access critical systems and data.
Understanding the Bigger Picture
There’s a positive trend in healthcare cybersecurity: threat actor dwell times and the amount of time attackers remain undetected in systems are dropping. This may result from security teams identifying breaches faster, which is cause to celebrate; however, it doesn’t paint the whole picture.
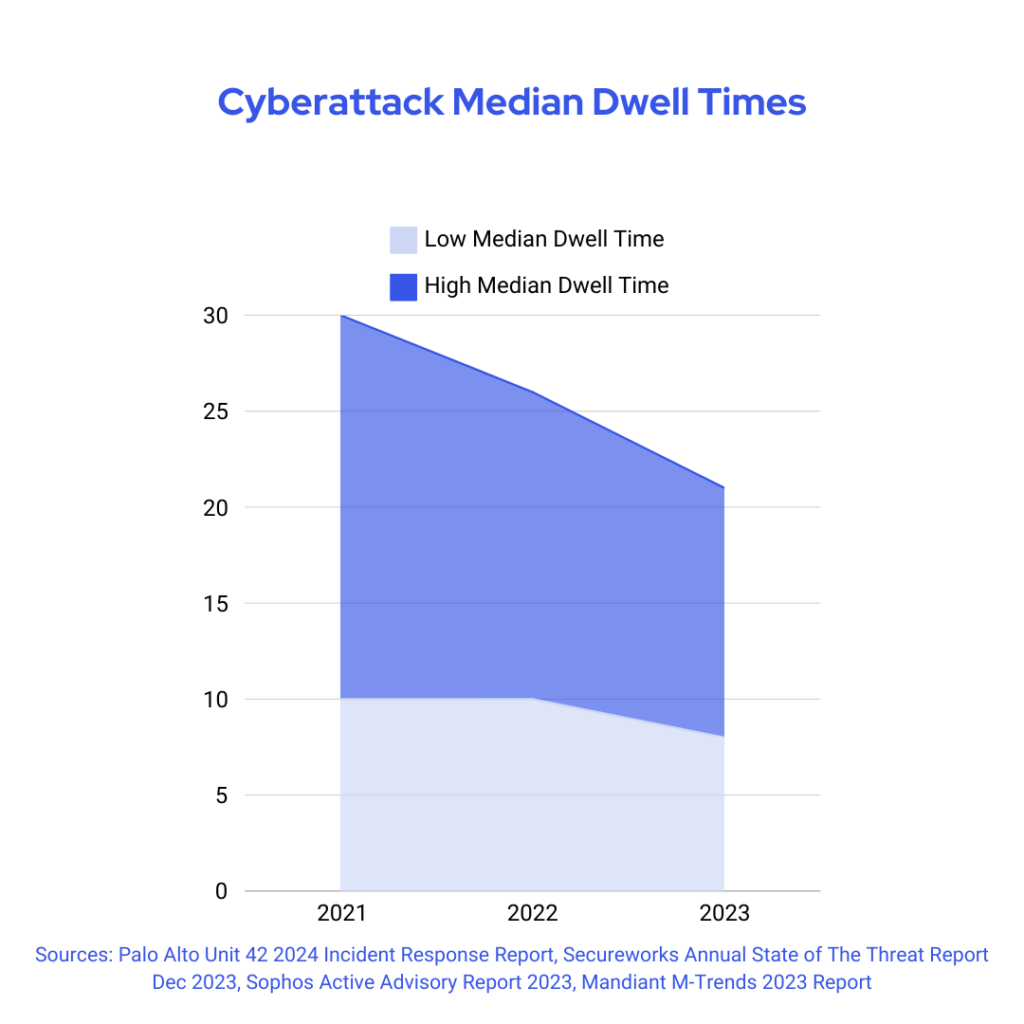
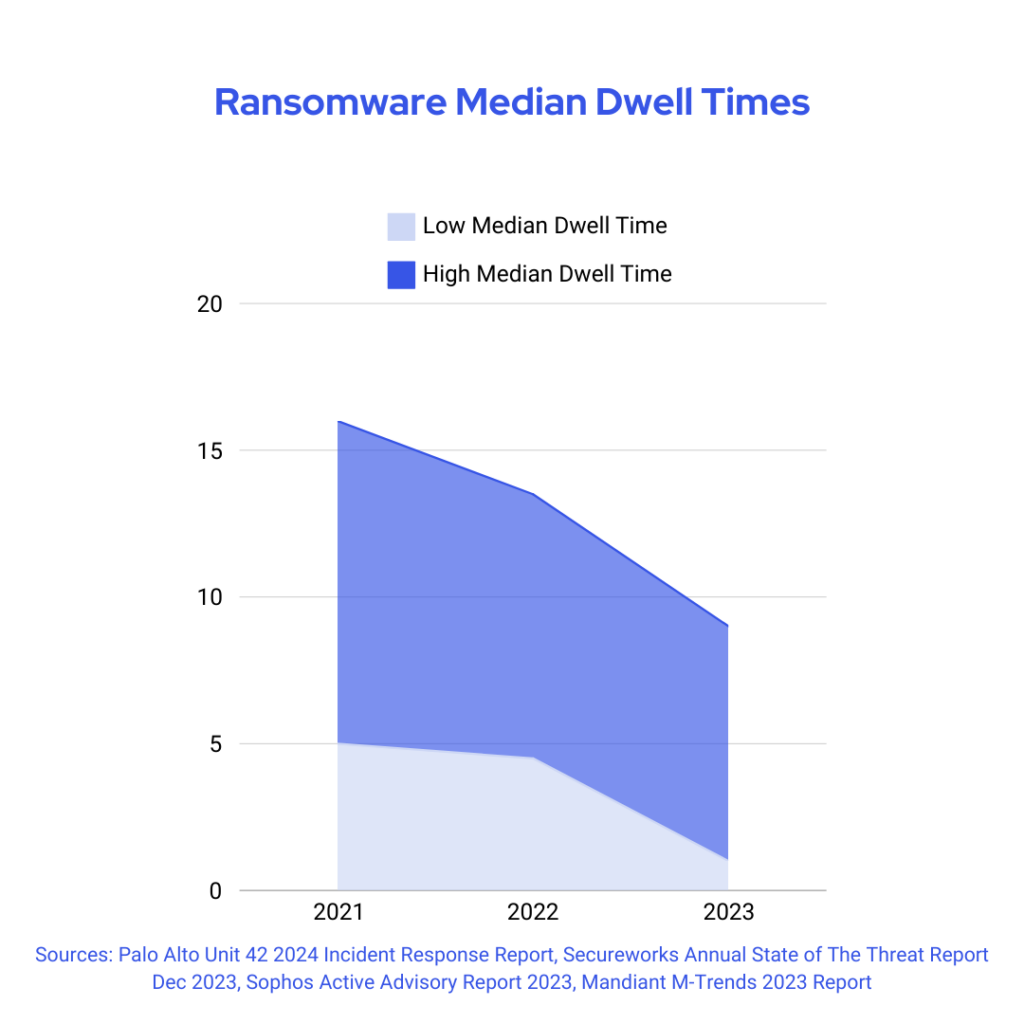
On the surface, those shorter dwell times seem positive, and on many fronts, they are. The decreased dwell time could be reflective of:
- More cybersecurity coverage
- Increased use of security tools and technologies
- Improvements in technologies to more effectively detect bad actors and malicious behaviors
- Increased use of managed security service providers (MSSPs)
- Increased security advisories and bulletins from partners, governing agencies, and, in many cases, alerts from the threat actors themselves about what they’re doing and which exploits and vulnerabilities they’re taking advantage of
But on the other hand, decreased dwell times could also mean that attackers are streamlining tactics and accelerating movements. In other words, even if caught sooner, they’re moving faster, potentially causing more damage before they’re stopped. Increased speed and stealth reduce the chance of detection. And, unlike previous attacks where threat actors wanted to linger as long as they could undetected for recognizance and data exfiltration, today, there are more instances of “grab and go” where attackers attempt to get as much access and data as they can and get out, focusing more on volume than data types.
In other words, although dwell times are decreasing, attack velocity and efficiency are increasing.
In 2022, the median time from attack compromise to exfil data was about nine days. In 2023, it was only two. Attackers deploy at least half of attacks in less than 24 hours, a time frame that used to take days or weeks. It only takes about 16 hours for an attacker to breach Active Directory (AD), where, once in, they can move laterally unnoticed, deploying malware and exfiltrating data, often undetected. That’s even easier to do considering more than 80% of ransomware attacks happen outside regular business hours and more than 40% occur on the weekend, at times there may be decreased internal awareness about system and network infiltration.
Protect Your Healthcare Organization
In addition to the recommendations issued by AHA and CISA, here are some other tips to help protect your business from further potential damage from the Change Healthcare breach and similar attacks.
If you haven’t done so already, immediately:
- Disconnect or block Change Healthcare and Optum connections until it’s confirmed safe to reconnect
- Continually check your environment for IoCs, especially ScreenConnect and Blackcat
- If you discover any IoCs, formally initiate incident response
- Conduct a compromise assessment
- Provide workforce awareness about potential scams and social engineering
- Continue to monitor threat alerts from CISA, Health Sector Cybersecurity Coordination Center (HC3)
- Leverage 405(d) Health Industry Cybersecurity Practices (HCIP), especially if your cybersecurity program is relatively new or immature
For a more sustained approach moving forward, consider:
- Risk management
- Determine criteria and establish risk tolerance to restore/unblock Change Healthcare/Optum connections.
- Know your current security posture.
- Ensure your IT/Security decision-makers are well-informed on relevant incident information.
- Cyber resilience (if you’re not currently managing a cyber incident)
- Validate and rehearse your plans
- Validate the effectiveness of your controls
- Provide continuous workforce awareness
- Minimum security capabilities
- Continuous security monitoring
- Use a security operations system (SOC)
- Employ endpoint detection and response (EDR) protections
- Enable logging
- Review scope and cadence of vulnerability management program and ensure capabilities are in place for rapid patching or implementing other mitigating controls.
- Conduct ongoing threat-hunting
- Update and test incident response plans
- Conduct a business impact analysis to feed into risk analysis and risk management programs.
- Review the impact of each system based on business or clinical process
- Include all systems, locations, and technologies for risk analysis
- Assess unique risks for each information system
- Conduct vendor risk assessments and ongoing vendor risk management
- Employ security measures like MFA and privilege access management



