Clearwater CEO Steve Cagle kicked off November’s Cyber Briefing with a threat intel update, providing healthcare leaders across the ecosystem with a review of the breach data and cybersecurity trends affecting healthcare organizations. Steve covered notable ransomware attacks, an update on the financial impact of ransomware and organizations publicly reporting costs of ransomware attacks, and new resources and recommendations.
Check back here throughout the month for additional updates, and if you’re not already registered for Clearwater’s monthly Cyber Briefings, be sure to do so here.
Healthcare Breaches Continue to Climb
After sharing that September was a relatively lighter month in reported breaches, it’s important to note that there’s often a lag in the data on the HHS breach portal. Breach numbers were added that more than doubled September’s numbers so while October also looks like a lighter month, we expect to see that number grow over the next few weeks as the data catches up.
As of November 1, we’re approaching 100M records breached over the last 12 months and a 62% increase in records breached of 2022 YTD.
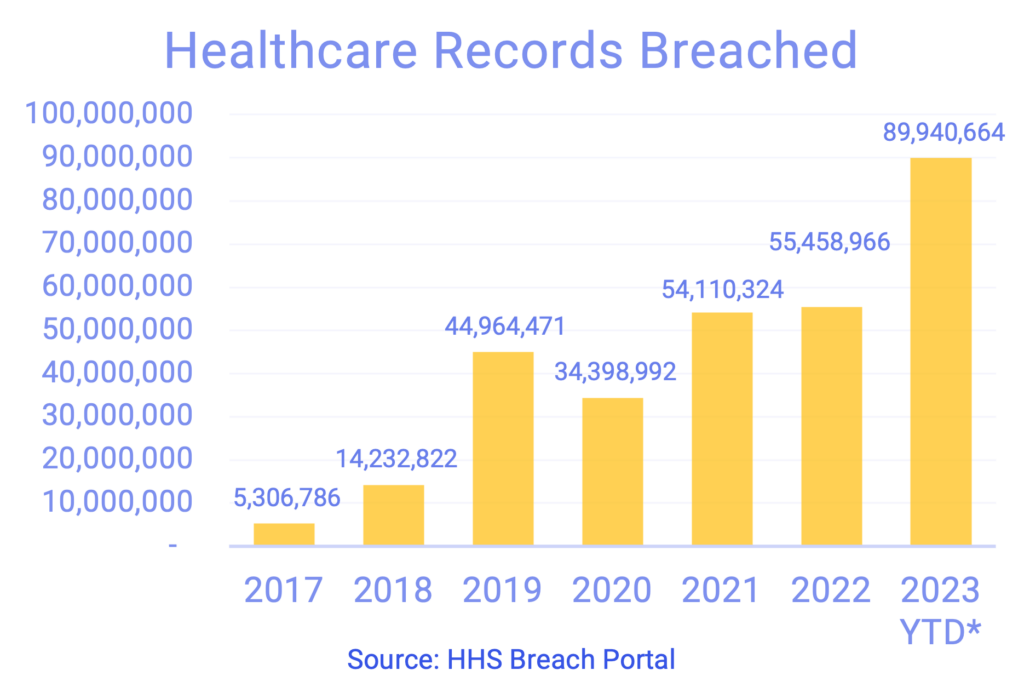
Notable Breaches
Arietis Health, a revenue cycle management company, reported approximately two million records breached in May of 2023 due to a CIOP/MoveIT ransomware attack. The breach affected 54 entities of Northstar Anesthesia, an Areitis Health customer. Northstar Anesthesia provides services to 200 hospitals across the country. This is an important breach because organizations must understand how big the impact can be when one partner or vendor is compromised. Further, like many attacks that take a long time to investigate, Arietis didn’t notify NorthStar Anesthesia until August and OCR until September. That lag time makes it difficult for the affected entities to act, so it’s important that healthcare covered entities clearly outline in BA agreements how and when reporting should take place in the event of a breach.
Health Network of Hudson Valley’s ransomware attack caused two hospitals to defer ambulances from their emergency rooms temporarily. They identified the problem on October 14th, then confirmed the attack on October 16th, and made a public announcement two weeks later. During those two weeks when some of the services were diverted, they had inpatients move to other facilities, a pretty extensive impact on patient care which created a bit of backlash. They shut down their operations or IT systems for 24 hours over the weekend and were able to get back online. We’ve talked a lot about resiliency and having incident response plans in place, making sure that all aspects, communication, technical components, and business continuity, all need to be exercised to ensure the organization can withstand and respond to an incident quickly.
Five Ontario hospitals are impacted by a cyber attack with their IT service provider, Transform, shared services, which it uses to run its IT systems, supply chain, accounting, and critical operations. At the time of November’s Cyber Briefing, it’s at least eight days since they’ve been impacted, and they’re still running on paper procedures. Most recent reports are that radiation treatments for cancer patients have been transferred to other hospitals, and payroll records are incorrect. In this case, we see that when five hospitals in one region are affected, it impacts an entire community and can overwhelm the hospitals that are absorbing transfers.
Akumin is a network of imaging centers that provides radiology and oncology services to approximately 1,000 hospitals in 48 States. Acumen is publicly traded and was recently forced to postpone most of its clinical and diagnostic services due to a ransomware attack. This was first reported on October 11th, and since then, it has gone through the process of announcing bankruptcy. This situation is not only because of the ransomware attack; the organization was already under financial stress, but this really put the organization over the edge. This is not the first time we’ve seen an organization go out of business due to a ransomware attack or breach.
Organizations Publicly Reporting Costs from Cyberattacks
- CommonSpirit, October 2022, a reported loss of $160 million
- Scripps Health, May 2021, a reported loss of $112.7 million
- Harvard Pilgrim Health Care (Point32Health), March 2023, a reported loss of $102.7 million
- Universal Health Services, September 2020, a reported loss of $67 million
- Bio-Rad Laboratories, Inc., December 2019, a reported loss of $20 million
- SmileDirectClub, April 2021, a reported loss of $15 million
- Erie County Medical Center, April 2017, a reported loss of $10 million
Threats to Mitigate in the Current Environment
- Business email compromise is increasing and becoming more convincing and elaborate. One specific tactic we’re seeing is bad actors tricking others into paying invoices or wiring money to a new account that doesn’t belong to the entity they think it does. This can have a high financial impact and be very difficult to get that money back.
- Credential stealing has become more sophisticated, using vishing, shmishing, and social engineering tactics that evade traditional security. Access brokers sometimes take this information and sell it to other organizations that use it for ransomware or other attacks.
- Zero-day vulnerabilities are being announced frequently. These vulnerabilities can be quickly exploited so it’s crucial that organizations have a good patch management program in place.
- Threat actors specifically target weak points—smaller organizations, financially weak organizations, and vendors/third parties that have fewer regulations (or are less likely to follow standards). It’s not hard for threat actors to spot the telltale signs of an organization that hasn’t invested in security.
- Insider threats are still an important concern and a large source of breaches.
- Cloud compromises are becoming more frequent and more impactful— cloud security is a specialized skill and can be difficult to manage without specialty help in-house or through a partner.
- The speed of a ransomware attack is now less than one day vs. an average of 4.5 days last year, leaving less time to detect and respond once a threat actor is in your environment. It’s essential that organizations can monitor and respond around the clock.
Additional Considerations
- Identify where all your ePHI is and ensure that you have thoroughly assessed individual risk scenarios and differences in controls between different applications or components based on their unique profiles.
- Engage the C-Suite and Board with current threat information and provide an executive-level overview of key risks based on your organization’s situation.
- Perform a risk assessment of your cloud environments and get assistance with remediating and optimizing security controls as needed.
- Consider risk with your MSP or IT Services provider.
- Determine whether you have too much concentration risk.
- Perform a detailed risk assessment and perform technical testing of the environment.
- Use a dedicated, expert-managed security services provider for Monitoring, Detection, and Response (MDR).
- Develop and test incident response plans, including involving stakeholders at the executive level.



